PRODUCTS
TSCM | TECHNICAL SURVEILLANCE COUNTER - MEASURES
THE THREATS ARE REAL
The search for illicit intelligence is a never-ending threat; from criminals trying to obtain information for financial gain, to sophisticated state-sponsored adversaries looking for political and military gains. While we do not always know what kind of threats are around us, a robust security policy encompassing physical security, cyber security and protection from electronic surveillance is needed to ensure that secrets remain secret.
The security of your building, your sensitive information, your private conversations, your plans and secrets can all be compromised by small, inexpensive surveillance devices and also drones.In some high security areas (like courts, R&D facilities, embassies, ministries etc.) also cellphones are not allowed and according to security policies the use of cellphones is illegal.
The 24/7 surveillance for illegal transmissions is mandatory.Modern surveillance technologies are highly discreet, highly capable and very difficult to locate. Even the smallest device can pack a considerable amount of technology.These devices can be integrated into USB cables, light bulbs or any number of other common objects.
When not in use, such a device can be on low power stand-by. Conversely, the device can collect and transmit data over very long periods of time via smart power management. If connected to a mobile network, it may only need to “shake hands” once every few hours (network defined); at other times it remains RF invisible.
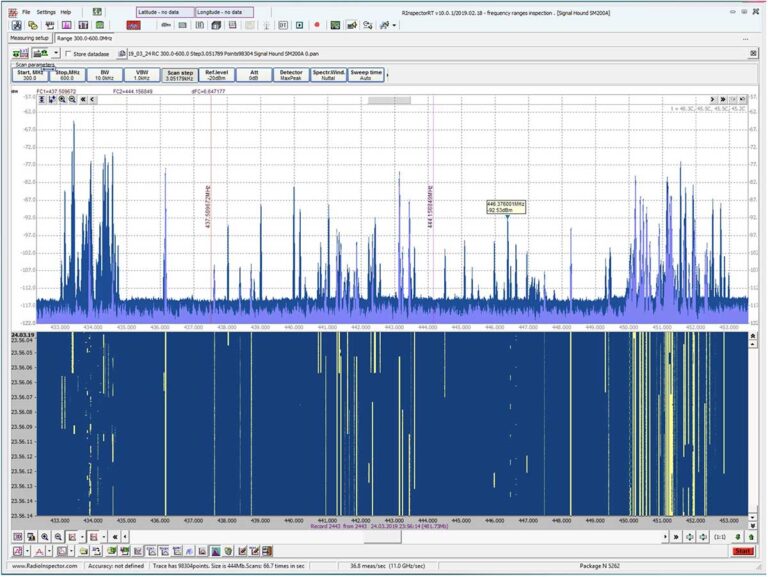
The traditional approach to detecting electronic surveillance devices (or bugs/ eavesdropping devices) is to use a hand-held bug sweeping tool. This tool is moved through a room to scan for the presence of a bug. However, bugs are often able to evade these sweeps. Devices that only transmit in short, infrequent bursts or frequency hopping, or devices that are “hidden” close or inside (below) to a high-power signal are just a few of examples of how eavesdropping devices can avoid detection by sweep teams. And of course, a device can be switched off during a sweep or placed after a sweep is conducted.
To provide complete assurance against RF surveillance, there is a need for continuous real-time TSCM in the form of an In-Place Monitoring System.
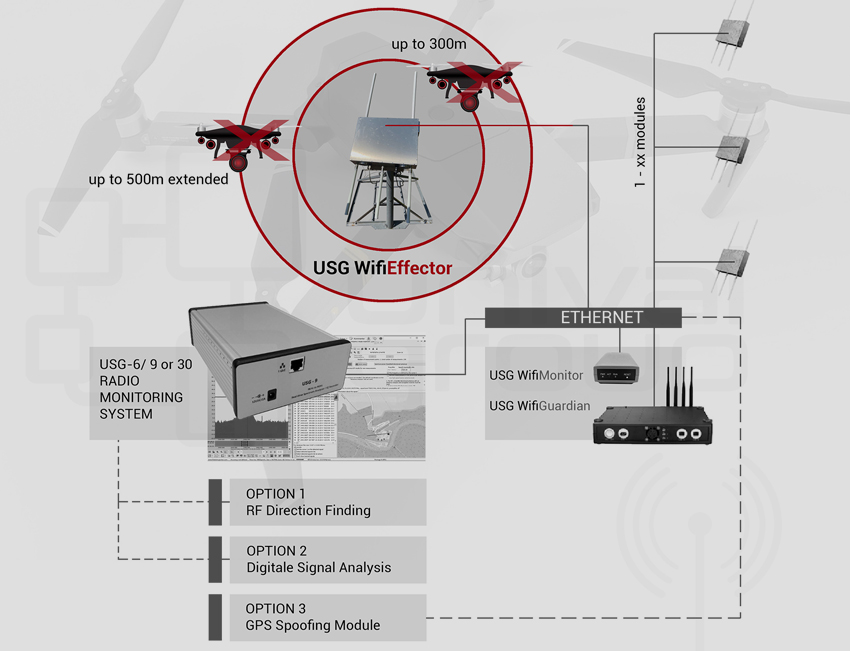
THIS IS WHERE THE unival USG SYSTEM COMES INTO PLAY
Fast sweep speeds and exceptionally low noise figures allow our USG sensors to detect even the lowest-power and shortest-duration signals.
These intelligent sensors, combined with the unival Spectrum Guard software suite, are operating autonomously and when a signal is detected, the unival USG system can provide a real-time analysis, an alert and location to a security guard in a command and control center and or send alerts by email, SMS or any other messenger.
unival USG can be deployed as a fixed installation or as a mobile solution.