TECHNOLOGY & TRAINING
THE unival ADDED VALUE FOR HIGH-LEVEL SECURITY
Today’s complex threat environment has already changed the technology procurement in the security industry. In order to master attacks both in the physical and digital sphere it is more important than ever to apply solutions that are adequately adjusted to the state of hybrid threats that are applied. The key challenge for industrial and governmental organizations is therefor to control a wide array of sensors and technologies that need to be firmly integrated and hardened for their specific use.
Existing solutions need to be designed and constructed in a way that they can be upgraded against future requirements. Technology cycles similar to Consumer electronics will become much shorter and since components from the consumer world are being used for attacks (UAVs & Co.) it is more important than ever to have an in-depth technology understanding and to choose the right counter measures.
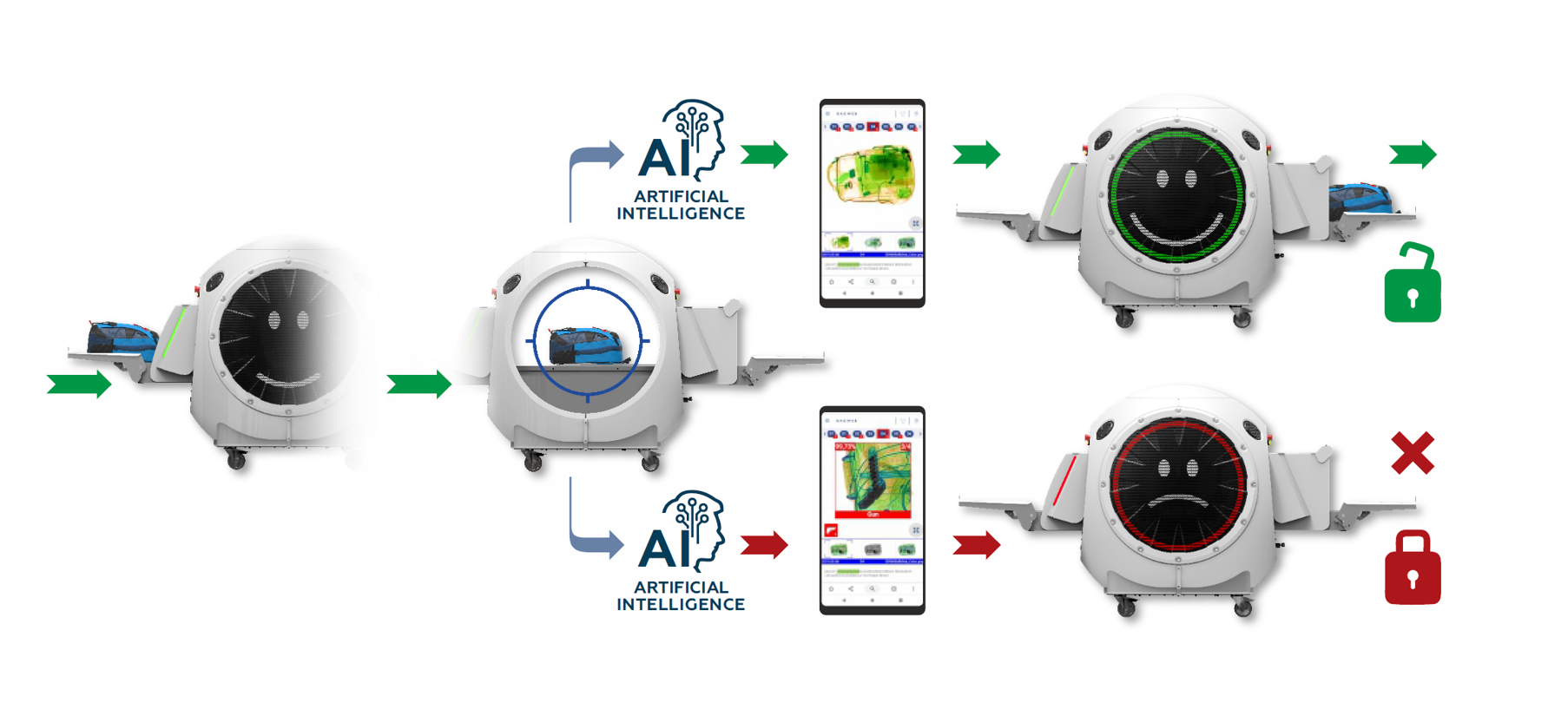
THE FUTURE OF SECURITY IS AI AND SPECIALISTS
WITH AI BASED DETECTION SUBJECT TO CLIENT SPECIFIC DATABASES, IT WILL BE POSSIBLE TO CHANGE THE SHAPE OF SECURITY.
So why is training such an important requirement especially for future operations? The answer is clear. While a majority of tasks will be carried out from lesser qualified staff, who are guided from a connected security command; highly qualified staff is necessary to handle all critical elements and to supervise operations.
Such specialized staff has to be trained with a much higher knowledge density and a deep understanding of the technologies being used as well as their best implementation and potential limitations. So a much higher technology training level has to be established with dedicated experts, who have deep operational skills even under critical conditions and based on deeply internalized procedures that are trained with a military-style intensive training.
Last but not least it should be clear that with threats from the asymmetric warfare approach, security has to also comprise of a strong risk management element that needs to include Cyber Security, Information Management and Counter Monitoring, Electronic Warfare, Secure Transportation, Key Management and many other security tasks. For this reason, a Security Coordinator has to constantly monitor threats and define threat levels on which basis procedures are being run. A Quick Response Force has to be considered for critical infrastructure and based on a vulnerability analysis, all weaknesses that could prevent continuous operation have to be identified and proactively prevented.
unival TACTICAL SITE PROTECTION
SECURITY IS A RESULT OF THREE MAJOR ELEMENTS:
TECHNOLOGY, PROCEDURES AND PEOPLE.
With professional security procedures in place, we are helping people to make the best possible use of available technology in order to master sophisticated security threats. Our Multi-Level Security Concept represents an organic and feasible combination of all security elements.
The best security equipment is not effectively usable, if no appropriate training is provided. With all of our security products comes an extensive tactical training program, ranging from operator level to service and maintenance level II. We make sure that our end users know how to use all of our systems at maximum efficiency. Training is provided at the client’s site, as well as in training facilities in Germany and factory site. Our training sessions always consist of theoretical and practical lessons, which are based on real scenarios and situations. Traditional learning is to gain extra knowledge, just to answer the “How” question. SMART learning is to answer “Why, when, how, and what” questions in meaningful sequence. A well-trained operator in many environments has a major impact on the level of success.
In industrial environments but also increasingly in civil security the introduction of outsourced security companies has led to a reduction of labor costs, which are naturally a major factor of consideration. However, we have seen an increase of low-paid unqualified security operators that have no real identification with their objective and who add a significant increase in human error. Any deviation from procedures defined in training must be documented and prevented. It should also be possible for a control center to influence procedures in the event of conspicuous anomalies, which requires efficient networking of all locations.
For this reason, it is highly important not only to monitor premises but also checkpoints and all areas where security operations take place. Regular stress tests have to carried out in order to make sure that continuous operations can be ensured. Such requirements are defined and described as part of a unival Site Assessment that can be ordered as part of the Scope of Work, which is the basis of our engagement.

